Secure Matrix LLC is aggressively enforcing US8677116B1 in a sweeping litigation campaign, targeting major companies across various industries. As a non-practicing entity (NPE), Secure Matrix LLC does not develop or sell products but instead leverages its patent portfolio to file infringement lawsuits. With 16 active cases and 67 related parties, the company has set its sights on well-known businesses like American Airlines, Sally Beauty Holdings, Rent-A-Center, and TGI Fridays, alleging unauthorized use of its patented technology.
At the core of US8677116B1 is a secure authentication system designed to verify user identities through multi-factor authentication (MFA), a widely used security measure that combines passwords, biometrics, and one-time passcodes. Secure Matrix LLC claims these companies are infringing by implementing authentication protocols that align with the patent’s claims. Given how essential authentication technology is in modern digital security, this case has far-reaching implications for businesses that rely on these systems.
With Secure Matrix LLC aggressively pursuing litigation across multiple industries, the key question is whether related patents exist that could challenge the validity of US8677116B1. If similar authentication methods were already in use before this patent was granted, it could weaken Secure Matrix LLC’s claims.
That is where Global Patent Search (GPS) becomes an essential tool. By identifying related patents, GPS enables legal teams to evaluate whether the patented invention was truly novel at the time of filing. In the following sections, we will break down the patent’s key features, examine related patents that might impact its validity, and explore what this could mean for ongoing litigation.
Understanding Patent US8677116B1
Secure Matrix LLC’s US8677116B1 focuses on systems and methods for authentication and verification that enhance secure access to digital and physical systems. The patent describes a process where a user attempts to access a secure capability, such as an online account, payment gateway, or physical lock. It undergoes authentication through multiple signals exchanged between their device, a verification server, and the system providing the secure capability.
At the core of this patent is a reusable identifier, which serves as a security token to verify the user. Unlike one-time passwords (OTPs) or traditional login credentials, this identifier is not transaction-specific. It can be reused within a defined period, allowing faster, more secure authentication. The technology aims to streamline user verification across websites, devices, and enterprise security systems, minimizing the risks of unauthorized access and fraud.
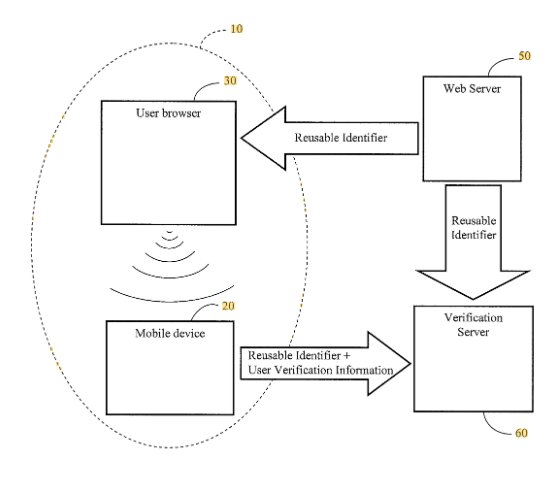
Source: Google Patents
Its four key features are:
#1. Reusable identifiers for authentication – A security token is issued for verifying users without containing transaction-specific or personal data, improving efficiency and security.
#2. Multi-signal verification process – Authentication requires multiple signals exchanged between the user’s device, the secure system, and a verification server, ensuring strong authentication before granting access.
#3. Cross-device authentication – The system enables users to verify themselves using one device (e.g., a smartphone) while accessing a secure system on another (e.g., a laptop or physical lock).
#4. Application in secure transactions – The patent extends to e-commerce payments, online account logins, and physical access control by allowing seamless authentication across different security-sensitive environments.
Secure Matrix LLC is asserting US8677116B1 against multiple companies that rely on authentication technologies to protect their platforms. Businesses in retail, travel, and hospitality, such as American Airlines, Sally Beauty Holdings, Rent-A-Center, and TGI Fridays, use multi-factor authentication (MFA) and secure login systems. Secure Matrix LLC claims infringe upon this patent. The widespread use of authentication systems across industries makes this litigation highly significant, as a ruling in Secure Matrix LLC’s favor could impact numerous businesses employing similar security measures.
Related Patent References for US8677116B1
#1. JP2003534589A
This patent, filed on May 23, 2001, describes an authentication system designed to verify user identity before granting access to secured equipment or services. The system utilizes a passcode that can either be a random number or a cryptographic digest, functioning similarly to the reusable identifier in US8677116B1. The authentication process involves multiple signals exchanged between the user’s device, a computer providing secured capabilities, and an authentication system.
Key Features of this Related Patent
- Computer system receiving an authentication request – The reference describes a system where a server receives authentication requests from a user, aligning with US8677116B1’s first authentication signal.
- Time-limited authentication credentials – JP2003534589A describes generating a session number valid for a finite period, which closely aligns with US8677116B1’s claim of assigning identifiers for a limited duration.
- Signal exchange between user’s device and authentication system – The patent outlines a process where the user’s mobile device sends a second authentication signal, mirroring US8677116B1’s two-step authentication process.
- Authorization decision based on received signals – A processor compares the passcode received from the user with the one generated by the system, determining authorization similarly to US8677116B1’s processor-based evaluation.
Which features of US8677116B1 are disclosed by JP2003534589A?
| Key Feature of Claim 1 | Disclosure Status |
| A computer system receives a first signal from a computer providing a secured capability | Fully Disclosed |
| The first signal includes a reusable identifier corresponding to the secured capability | Partially Disclosed |
| The reusable identifier is assigned for use by the secured capability for a finite period of time | Fully Disclosed |
| The computer system receives a second signal from a user’s electronic device | Fully Disclosed |
| The second signal includes a copy of the reusable identifier | Fully Disclosed |
| The second signal includes user verification information | Partially Disclosed |
| A processor evaluates whether the user is authorized based on the first and second signals | Fully Disclosed |
| The computer system transmits a third signal with authorization information when the user is authorized | Fully Disclosed |
| The third signal is sent to either the electronic device or the computer | Fully Disclosed |
Key excerpt from JP2003534589A:
“When the user receives the passcode on their mobile communication device, the passcode is used as a key for gaining access to the secure service provided by the server. The system evaluates the received passcode against the generated one and grants or denies access accordingly.”
#2. US20030046541A1
This patent, filed on August 22, 2002, describes a universal authentication mechanism that enables secure access to services by verifying a user’s identity through an authentication server. The system operates by receiving authentication requests from a service provider and validating user credentials via an authentication device. The method ensures that access is granted only after successful verification, aligning with the authentication principles of US8677116B1.
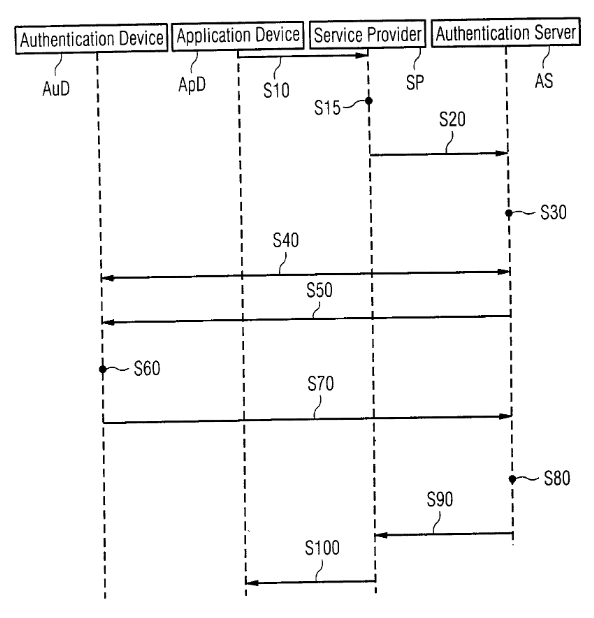
Source: GPS
Key Features of This Related Patent
- Authentication request from a service provider – The system requires authentication before granting access, similar to US8677116B1’s process of receiving a first authentication signal.
- User verification using passwords or PINs – The reference confirms user identity through additional verification methods, aligning with US8677116B1’s requirement for user verification information.
- Authorization decision based on authentication signals – The authentication server analyzes user credentials before granting access, comparable to US8677116B1’s processor-based authorization evaluation.
- Transmission of authorization confirmation – Upon successful authentication, a third signal is sent confirming access, similar to US8677116B1’s transmission of authorization information.
Which features of US8677116B1 are disclosed by US20030046541A1?
| Key Feature of Claim 1 | Disclosure Status |
| A computer system receives a first signal from a computer providing a secured capability | Fully Disclosed |
| The first signal includes a reusable identifier corresponding to the secured capability | Partially Disclosed |
| The computer system receives a second signal from a user’s electronic device | Fully Disclosed |
| The second signal includes user verification information | Fully Disclosed |
| A processor evaluates whether the user is authorized based on the first and second signals | Fully Disclosed |
| The computer system transmits a third signal with authorization information when the user is authorized | Fully Disclosed |
| The third signal is sent to either the electronic device or the computer | Partially Disclosed |
Key excerpt from US20030046541A1:
“In the proposed method, an application device requests a service for a user from a service provider. Before granting access, the service provider requires authentication of the user, which is validated through an authentication server. The server then confirms or denies access based on the authentication response.”
#3. US7233997B1
This patent, filed on June 26, 1998, describes a data communication system that authenticates users before granting access to secured digital resources. The system issues a session identifier to a client terminal upon authentication, which is then used to validate future access requests. The session identifier, similar to US8677116B1’s reusable identifier, ensures secure access control by verifying user credentials through a structured multi-step process.
Key Features of this Related Patent
- Session-based authentication for secure access – The system assigns a session identifier to authenticate users, aligning with US8677116B1’s reusable identifier approach.
- Time-limited authentication credentials – The session identifier is valid for a predetermined duration, closely matching US8677116B1’s method of assigning identifiers for a finite period.
- Multi-step verification process – The system validates user identity through a series of authentication exchanges, similar to US8677116B1’s signal-based authorization process.
- Transmission of authorization confirmation – Upon successful validation, the system grants access by sending authorization data to the user’s terminal, aligning with US8677116B1’s third signal transmission.
Which features of US8677116B1 are disclosed by US7233997B1?
| Key Feature of Claim 1 | Disclosure Status |
| A computer system receives a first signal from a computer providing a secured capability | Fully Disclosed |
| The first signal includes a reusable identifier corresponding to the secured capability | Fully Disclosed |
| The reusable identifier is assigned for use by the secured capability for a finite period of time | Fully Disclosed |
| The computer system receives a second signal from a user’s electronic device | Fully Disclosed |
| The second signal includes a copy of the reusable identifier | Fully Disclosed |
| The second signal includes user verification information | Partially Disclosed |
| A processor evaluates whether the user is authorized based on the first and second signals | Fully Disclosed |
| The computer system transmits a third signal with authorization information when the user is authorized | Fully Disclosed |
| The third signal is sent to either the electronic device or the computer | Fully Disclosed |
Key excerpt from US7233997B1:
“The authentication server performs authentication of a client terminal and then issues a session identification (SID) to the terminal. This SID is valid for a predetermined period and is used to authorize document access by verifying user credentials.”
#4. US20020091945A1
This patent, filed on October 30, 2001, describes a verification engine for user authentication that improves security by analyzing user responses to predefined queries. The system does not rely on traditional authentication credentials such as passwords or digital signatures, making it more flexible and adaptive. Instead, it compares user-provided data with information stored in independent databases before granting access.
Key Features of this Related Patent
- Authentication based on predefined queries – Instead of traditional login credentials, the system verifies user identity by analyzing responses to specific queries, aligning with US8677116B1’s user verification process.
- Processor-driven authentication evaluation – The verification engine processes collected user data and compares it against stored records, similar to US8677116B1’s evaluation of authentication signals.
- Transmission of authentication results – The system sends a confidence score or verification decision to the authentication client, comparable to US8677116B1’s third signal transmission.
- Alternative verification mechanism – Unlike conventional methods relying on passwords or PINs, this patent introduces an adaptive authentication model, partially overlapping with US8677116B1’s authentication approach.
Here’s what the mapping from the tool for this particular patent looks like:
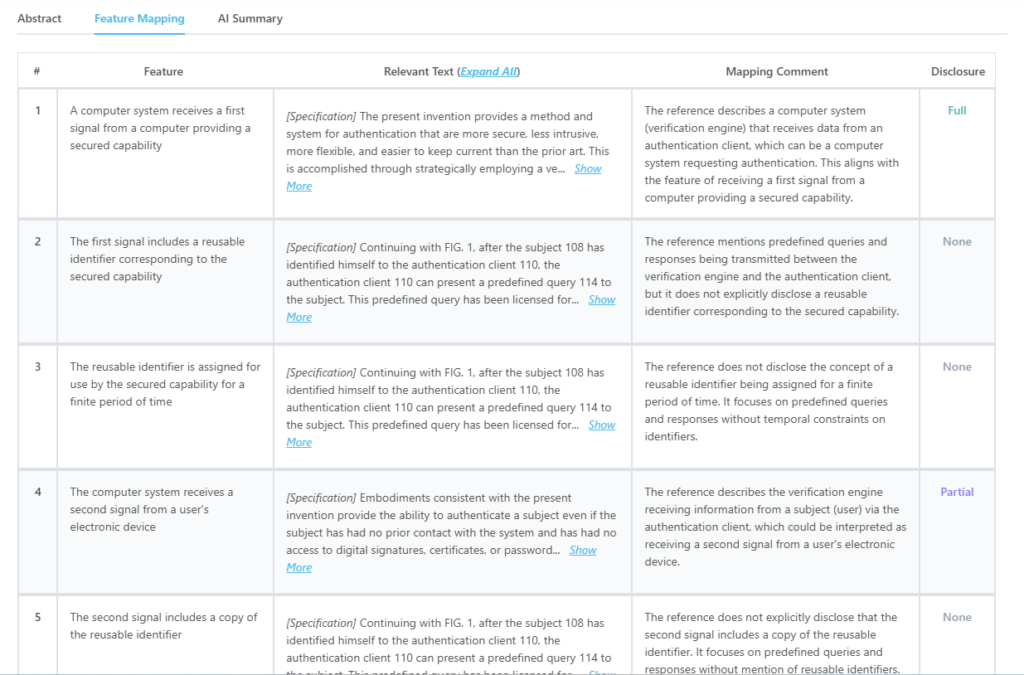
Source: GPS
Which features of US8677116B1 are disclosed by US20020091945A1?
| Key Feature of Claim 1 | Disclosure Status |
| A computer system receives a first signal from a computer providing a secured capability | Fully Disclosed |
| The computer system receives a second signal from a user’s electronic device | Partially Disclosed |
| The second signal includes user verification information | Partially Disclosed |
| A processor evaluates whether the user is authorized based on the first and second signals | Fully Disclosed |
| The computer system transmits a third signal with authorization information when the user is authorized | Fully Disclosed |
| The third signal is sent to either the electronic device or the computer | Partially Disclosed |
Key excerpt from US20020091945A1:
“The verification engine accepts personal data from a subject being authenticated. The system then cross-references the data against independent databases and transmits a confidence score to the authentication client to determine whether access should be granted.”
#5. US20020184496A1
This patent, filed on April 16, 2001, describes a system for managing parental access consent in a network environment. It allows authentication servers to validate user credentials and transmit authorization decisions to affiliate servers, ensuring that access is granted based on predefined criteria. The process involves exchanging signals containing validation codes and user credentials, aligning with the authentication framework of US8677116B1.
Key Features of this Related Patent
- Authentication using validation codes – The system transmits validation codes between authentication servers and affiliate servers to manage access, similar to US8677116B1’s reusable identifier concept.
- Time-restricted authorization credentials – The validation codes are valid for a specified period, aligning with US8677116B1’s assignment of identifiers for finite durations.
- Multi-signal authentication process – The user’s device sends signals containing identifiers and verification credentials, mirroring US8677116B1’s two-step authentication.
- Transmission of authorization decisions – Once authentication is verified, the system sends approval signals to either the user’s device or an affiliate server, aligning with US8677116B1’s third signal transmission.
Which features of US8677116B1 are disclosed by US20020184496A1?
| Key Feature of Claim 1 | Disclosure Status |
| A computer system receives a first signal from a computer providing a secured capability | Fully Disclosed |
| The first signal includes a reusable identifier corresponding to the secured capability | Fully Disclosed |
| The reusable identifier is assigned for use by the secured capability for a finite period of time | Fully Disclosed |
| The computer system receives a second signal from a user’s electronic device | Fully Disclosed |
| The second signal includes a copy of the reusable identifier | Fully Disclosed |
| The second signal includes user verification information | Fully Disclosed |
| A processor evaluates whether the user is authorized based on the first and second signals | Fully Disclosed |
| The computer system transmits a third signal with authorization information when the user is authorized | Fully Disclosed |
| The third signal is sent to either the electronic device or the computer | Fully Disclosed |
Key excerpt from US20020184496A1:
“In accordance with certain exemplary implementations, consent information is obtained from a first party, allowing a second party access to a network server that requires such consent information. Validation codes and member IDs are exchanged between authentication servers and affiliate servers to ensure secure access.”
Feature Comparison Table
| Key Features of Claim 1 | JP2003534589A | US20030046541A1 | US7233997B1 | US20020091945A1 | US20020184496A1 |
| A computer system receives a first signal from a computer providing a secured capability | Fully Disclosed | Fully Disclosed | Fully Disclosed | Fully Disclosed | Fully Disclosed |
| The first signal includes a reusable identifier corresponding to the secured capability | Partially Disclosed | Partially Disclosed | Fully Disclosed | Not Disclosed | Fully Disclosed |
| The reusable identifier is assigned for use by the secured capability for a finite period of time | Fully Disclosed | Not Disclosed | Fully Disclosed | Not Disclosed | Fully Disclosed |
| The computer system receives a second signal from a user’s electronic device | Fully Disclosed | Fully Disclosed | Fully Disclosed | Partially Disclosed | Fully Disclosed |
| The second signal includes a copy of the reusable identifier | Fully Disclosed | Not Disclosed | Fully Disclosed | Not Disclosed | Fully Disclosed |
| The second signal includes user verification information | Partially Disclosed | Fully Disclosed | Partially Disclosed | Partially Disclosed | Fully Disclosed |
| A processor evaluates whether the user is authorized based on the first and second signals | Fully Disclosed | Fully Disclosed | Fully Disclosed | Fully Disclosed | Fully Disclosed |
| The computer system transmits a third signal with authorization information when the user is authorized | Fully Disclosed | Fully Disclosed | Fully Disclosed | Fully Disclosed | Fully Disclosed |
| The third signal is sent to either the electronic device or the computer | Fully Disclosed | Partially Disclosed | Fully Disclosed | Partially Disclosed | Fully Disclosed |
How to Find Related Patents Using Global Patent Search
Finding related patents is essential in assessing the strength and validity of a patent in litigation. The Global Patent Search (GPS) tool simplifies this process by providing a structured and efficient way to identify patents with similar features.
- Search by patent number or description – Enter the target patent number (e.g., US8677116B1) or relevant keywords to retrieve related patents.
Source: GPS
- Leverage feature mapping – GPS automatically maps key features of the subject patent against existing patents to highlight similarities.
- Review matching results – The tool generates a list of relevant patents, ranked based on their similarity to the target patent.
- Analyze detailed reports – Each related patent is mapped against the subject patent’s claims, showing whether key features are fully, partially, or not disclosed.
- Make informed decisions – Use the structured comparison data to strengthen legal arguments, refine invalidity contentions, or assess infringement risks.
By utilizing Global Patent Search, professionals can save time and enhance the accuracy of their patent analysis, ensuring that they uncover the most relevant prior disclosures efficiently.
Take the Guesswork Out of Patent Research
Patent disputes demand precision, and finding the right related patents can be the key to winning a case. The Global Patent Search (GPS) tool empowers you with:
- Instant, AI-powered results – Skip the manual search and uncover critical patents in seconds.
- Comprehensive feature mapping – Get a precise, side-by-side breakdown of overlapping technologies.
- Data-driven legal strategy – Strengthen your case with structured, verifiable patent comparisons.
Don’t leave your litigation strategy to chance. Gain the competitive edge with Global Patent Search. Start your search today!
Disclaimer: The information provided in this article is for informational purposes only and should not be considered legal advice. The related patent references mentioned are preliminary results from the Global Patent Search (GPS) tool and do not guarantee legal significance. For a comprehensive related patent analysis, we recommend conducting a detailed search using GPS or consulting a patent attorney.