Could dozens of companies be facing legal challenges over a single patent? That seems to be the case with Torus Ventures LLC, a non-practicing entity (NPE) that has aggressively asserted patent US7203844B1 in over 140 lawsuits, with 81 currently active. The defendants span multiple industries, including insurance companies, banks, restaurant chains, and tech firms, making this one of the broadest enforcement campaigns in recent years.
This patent, originally granted in 2007, pertains to secure electronic transactions over distributed computer networks. In simple terms, it describes a way to authenticate users and encrypt communications in online transactions. The technology aims to enhance security when exchanging sensitive data, something that is fundamental in banking, insurance, and e-commerce.
With cyber threats rising, businesses rely heavily on secure login systems, encrypted communications, and transaction verification. Many companies have implemented authentication methods that resemble the techniques described in US7203844B1. Torus Ventures LLC now claims these businesses infringe on their patented method, leading to widespread litigation.
Given the extensive legal battle unfolding, one key question arises: Is there a related patent that could challenge the validity of US7203844B1? Identifying earlier patents or publications that disclose similar authentication methods could be crucial in defending against these lawsuits.
In the next section, we’ll break down the core features of this patent, followed by a detailed related patent analysis to assess whether Torus Ventures’ claims hold up against existing technology.
Understanding Patent US7203844B1
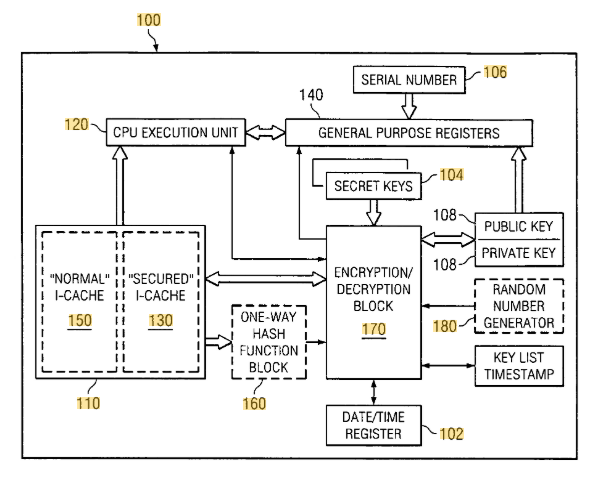
Patent US7203844B1, titled “Method and System for a Recursive Security Protocol for Digital Copyright Control,” focuses on securing digital content through a multi-layered encryption technique. It describes a method where a bitstream (digital data) is encrypted multiple times using different encryption algorithms, with each layer of encryption incorporating its own decryption process. This approach enhances digital rights management (DRM), ensuring that only authorized users can access and use protected digital content.
Source: Google Patents
Its key features are:
#1. Recursive encryption mechanism – The patent introduces a layered security model, where a digital file is encrypted, then encrypted again with an additional layer of security, creating a multi-level protection system.
#2. Authentication & access control – The system assigns decryption algorithms and unique keys to each encryption layer, ensuring that only authorized users with valid credentials can access the protected data.
#3. Tamper-resistant key management – Encryption keys are stored securely, either within hardware or on a remote server, preventing unauthorized access or key manipulation.
#4. Self-updating security protocols – The system allows for security updates without requiring changes to hardware, meaning newer encryption layers can be applied on top of existing ones to reinforce protection.
This patent is being asserted in litigation by Torus Ventures LLC, a non-practicing entity, against companies that handle digital transactions, secure communications, and DRM-based content protection. The widespread enforcement of this patent suggests that any business employing multi-layer encryption in DRM or secure access systems may be targeted.
Potential Related Patent Reference for US7203844B1
#1. EP0893763A1
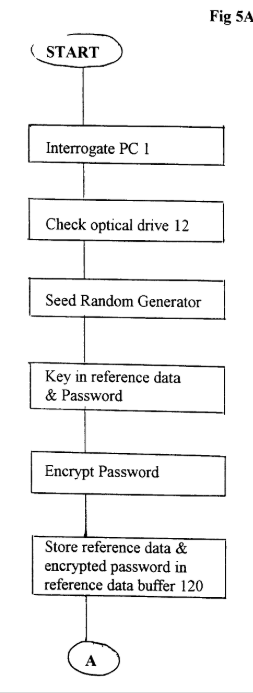
This patent, filed on July 3, 1998, describes a system for ensuring the integrity and authentication of digital data, particularly in computer forensics. It involves generating hash values for data blocks, encrypting them for security, and verifying data integrity using cryptographic methods. While it focuses on forensic data protection, its use of encryption layers and verification mechanisms aligns with certain aspects of US7203844B1.
Source: GPS
Key Features of this Related Patent:
- Recursive data protection via encryption – The reference discusses encrypting hash values and using multiple levels of cryptographic security, which aligns with US7203844B1’s approach to data protection through encryption layers.
- Integrity verification with encrypted hash values – The patent describes encrypting data integrity values (hashes) for validation, a concept related to the multi-layered encryption approach in US7203844B1.
- Use of encryption for secure data storage – While the reference does not explicitly disclose a recursive encryption process, it utilizes encryption for securing digital data copies, overlapping with some concepts in US7203844B1.
Which features of US7203844B1 are disclosed by EP0893763A1?
| Key feature of claim 1 | Disclosure status |
| A method for a recursive security protocol for protecting digital content | Partially disclosed |
| Encrypting a bitstream with a first encryption algorithm | Partially disclosed |
| Associating a first decryption algorithm with the encrypted bitstream | Partially disclosed |
Key excerpt from EP0893763A1:
“Once all the memory data has been copied to the optical cartridge 101(1), then another hash value – known as the IVAS block hash value #(n) – is generated from all the other hash values #(3)….(n-1) stored in the IVAS buffer.”
#2. TW545020B
This patent, filed on September 13, 2000, describes a method for securing digital content by employing multi-layer encryption and decryption techniques. The invention allows multiple companies to encrypt an original object into layered encrypted objects, preventing unauthorized copying and enabling secure content distribution. This method aligns closely with the recursive encryption framework described in US7203844B1.
Key Features of this Related Patent:
- Layered encryption methodology – The reference describes a step-by-step encryption process where data is encrypted into multiple layers, matching the recursive security protocol concept in US7203844B1.
- Encryption and decryption pairing – The invention explicitly associates decryption algorithms with encrypted layers, ensuring that only authorized users can access content, aligning with US7203844B1’s structure.
- Protection against unauthorized copying – The patent aims to prevent illegal replication of digital content, reinforcing the copyright control mechanism central to US7203844B1.
Which features of US7203844B1 are disclosed by TW545020B?
| Key feature of claim 1 | Disclosure status |
| A method for a recursive security protocol for protecting digital content | Fully disclosed |
| Encrypting a bitstream with a first encryption algorithm | Fully disclosed |
| Associating a first decryption algorithm with the encrypted bitstream | Fully disclosed |
| Encrypting both the encrypted bitstream and the first decryption algorithm with a second encryption algorithm to yield a second bitstream | Fully disclosed |
| Associating a second decryption algorithm with the second bitstream | Fully disclosed |
Key excerpt from TW545020B:
“Another method for security control of the production right of the present invention relates to a method in which multiple companies can prevent the unauthorized copying of the original object and sell the original object on the market by encrypting the first-layer encrypted object into a second-layer encrypted object.”
#3. KR100493284B1
This patent, filed on April 18, 2002, describes a hybrid cryptographic method for digital media protection and duplication control. The invention utilizes multi-layer encryption techniques to prevent unauthorized copying and authenticating digital media through encryption keys and decryption processes. While it does not explicitly mention a recursive security protocol, its layered encryption and decryption approach shares similarities with US7203844B1.
Key Features of this Related Patent:
- Layered encryption for media protection – The reference describes multiple levels of encryption, similar to US7203844B1’s recursive security protocol.
- Encrypted media authentication – It outlines a system where decryption keys are linked to encrypted data, aligning with US7203844B1’s concept of associating encryption and decryption steps.
- Hybrid cryptographic approach – The invention combines symmetric and asymmetric encryption methods, ensuring secure media duplication control, which is partially aligned with US7203844B1’s encryption methodology.
Which features of US7203844B1 are disclosed by KR100493284B1?
| Key feature of claim 1 | Disclosure status |
| A method for a recursive security protocol for protecting digital content | Partially disclosed |
| Encrypting a bitstream with a first encryption algorithm | Fully disclosed |
| Associating a first decryption algorithm with the encrypted bitstream | Fully disclosed |
| Encrypting both the encrypted bitstream and the first decryption algorithm with a second encryption algorithm to yield a second bitstream | Partially disclosed |
| Associating a second decryption algorithm with the second bitstream | Partially disclosed |
Key excerpt from KR100493284B1:
“The present invention relates to a digital media data duplication control method and system that substantially solves problems caused by limitations and disadvantages of the prior art. It is an object of the present invention to encrypt a media data set using a symmetric algorithm and then encrypt the decryption key with a public key to ensure secure access control.”
#4. JP2003229850A
This patent, filed on January 31, 2002, describes a one-way authentication protocol for securing communication between parties. The invention involves generating cryptographic inspection information, encrypting it with a shared secret key, and verifying it upon receipt to confirm the communication partner’s identity. While it focuses on authentication, its cryptographic operations share some conceptual similarities with US7203844B1.
Key Features of this Related Patent:
- Security protocol for data protection – The reference describes a security mechanism that encrypts transmitted data for verification and authentication, similar to US7203844B1’s goal of securing digital content.
- Encryption and decryption processes – It involves encrypting and decrypting cryptographic inspection information, aligning with the encryption-based protection framework in US7203844B1.
- Key-based cryptographic verification – The use of a shared secret key (Kc) for encryption and decryption partially aligns with the key association mechanism described in US7203844B1.
Here’s what the mapping from the tool for this particular patent looks like:
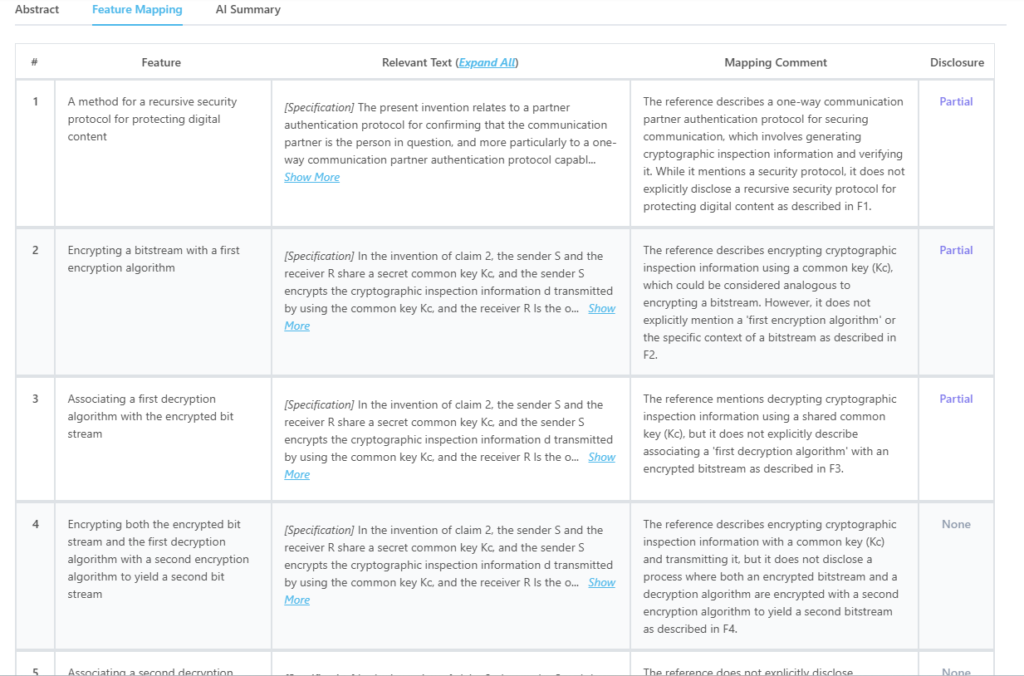
Source: GPS
Which features of US7203844B1 are disclosed by JP2003229850A?
| Key feature of claim 1 | Disclosure status |
| A method for a recursive security protocol for protecting digital content | Partially disclosed |
| Encrypting a bitstream with a first encryption algorithm | Partially disclosed |
| Associating a first decryption algorithm with the encrypted bitstream | Partially disclosed |
Key excerpt from JP2003229850A:
“The sender S and the receiver R share a secret common key Kc, and the sender S encrypts the cryptographic inspection information transmitted using the common key Kc. The receiver R is the only entity able to decrypt and verify it.”
#5. TW401562B
This patent, filed on January 31, 1997, describes a method for protecting digital content by using electronic signatures and encryption to verify and control data writing into a protected non-volatile storage device. The system ensures data integrity by generating a cryptographic digest and using a decryption function for verification before allowing the data to be written. While the primary focus is on secure storage, its recursive verification process and cryptographic techniques share key similarities with US7203844B1.
Key Features of this Related Patent:
- Recursive security and verification – The reference describes a layered verification process where data integrity is checked before storage, aligning with US7203844B1’s recursive security concept.
- Encryption of digital content – It involves encrypting a data digest before storage, partially aligning with the encryption principles in US7203844B1.
- Decryption-based authentication – The system uses a decryption function to verify stored data, similar to how US7203844B1 handles decryption for security enforcement.
Which features of US7203844B1 are disclosed by TW401562B?
| Key feature of claim 1 | Disclosure status |
| A method for a recursive security protocol for protecting digital content | Fully disclosed |
| Encrypting a bitstream with a first encryption algorithm | Partially disclosed |
| Associating a first decryption algorithm with the encrypted bitstream | Fully disclosed |
Key excerpt from TW401562B:
“The protected verification function includes a protected counterpart copy of the message digest function and a protected complementary decryption function. During operation, the protected decryption function reconstructs the original message digest to authenticate the written data before it is stored.”
Feature Comparison Table
| Key Feature of US7203844B1 | TW401562B | JP2003229850A | KR100493284B1 | TW545020B | EP0893763A1 |
| A method for a recursive security protocol for protecting digital content | Fully Disclosed | Partially Disclosed | Partially Disclosed | Fully Disclosed | Partially Disclosed |
| Encrypting a bitstream with a first encryption algorithm | Partially Disclosed | Partially Disclosed | Fully Disclosed | Fully Disclosed | Partially Disclosed |
| Associating a first decryption algorithm with the encrypted bit stream | Fully Disclosed | Partially Disclosed | Fully Disclosed | Fully Disclosed | Partially Disclosed |
| Encrypting both the encrypted bit stream and the first decryption algorithm with a second encryption algorithm to yield a second bit stream | Not Disclosed | Not Disclosed | Partially Disclosed | Fully Disclosed | Not Disclosed |
| Associating a second decryption algorithm with the second bit stream | Not Disclosed | Not Disclosed | Partially Disclosed | Fully Disclosed | Not Disclosed |
How to Identify Related Patents Using Global Patent Search?
Finding related patents is essential for assessing a patent’s scope and validity. The Global Patent Search (GPS) tool simplifies this process by delivering comprehensive, data-driven insights. Here’s how you can efficiently discover relevant related patents:
Search by patent number or description – Instantly locate patents by entering specific claims, technology fields, or key terms.

Source: GPS
Utilize feature mapping – Compare critical features of the target patent with existing ones using automated mapping to highlight similarities and distinctions.
Evaluate matching results – The system generates a prioritized list of related patents, ensuring that the most technologically relevant references are identified.
Examine detailed reports – Each reference includes an analysis of mapped features, disclosure levels, and direct excerpts, allowing for a thorough comparison of patent claims.
Make informed decisions – GPS offers data-backed insights to help legal professionals refine patent evaluations and litigation strategies with accuracy.
With Global Patent Search, you can streamline your research and confidently identify the most relevant related patents.
Stop Guessing: Find Related Patents That Matter
Patent disputes are a battlefield; don’t walk in unarmed. With Global Patent Search (GPS), you get:
- Lightning-fast results – No more digging through endless archives. Get the patents you need in seconds.
- Pinpoint accuracy – Our cutting-edge feature mapping zeroes in on key overlaps between the subject patent and existing references.
- Powerful data-driven insights – Build an ironclad case with detailed comparisons, disclosure reports, and expert-backed analysis.
When every detail counts, don’t leave anything to chance. Arm yourself with the best related patents; Start searching with GPS today!
Disclaimer: The information provided in this article is for informational purposes only and should not be considered legal advice. The related patent references mentioned are preliminary results from the Global Patent Search (GPS) tool and do not guarantee legal significance. For a comprehensive related patent analysis, we recommend conducting a detailed search using GPS or consulting a patent attorney.