Patent US7233664B2, titled “Dynamic Security Authentication for Wireless Communication Networks,” is central to Encryptawave Technologies LLC’s litigation efforts. This patent outlines a method for secure authentication between wireless network nodes, focusing on dynamic encryption and synchronization techniques to enhance security.
Encryptawave Technologies LLC has initiated multiple lawsuits alleging infringement of this patent. Currently, six cases are active, including those against Sercomm Corporation and Toshiba Corporation. Eight additional cases have been terminated.
Understanding the specifics of Patent US7233664B2 is crucial in assessing its role and potential challenges in these legal proceedings.
Understanding Patent US7233664B2
Patent US7233664B2 describes a security system that enhances authentication between network nodes through dynamic encryption and full synchronization. The invention addresses vulnerabilities in traditional cryptographic systems by continuously modifying encryption keys and using synchronized authentication methods. The goal is to prevent security breaches, particularly from insider attacks, and ensure secure data transmission between wireless devices.
Its four key features are:
#1. Dynamic session key regeneration – Every data record is encrypted with a continuously changing encryption key, making it difficult for attackers to compromise security.
#2. Central authority-based authentication – A central server (authentication authority) synchronizes and validates the security keys between network nodes.
#3. Secure wireless handovers – The system supports seamless authentication when a device moves between network access points, ensuring uninterrupted, secure communication.
#4. Protection against insider attacks – Unlike static encryption systems, this patent implements real-time authentication key updates to counteract threats from privileged insiders or intercepted keys.
US7233664B2 is a critical patent in Encryptawave Technologies LLC’s litigation campaign, which involves six active and eight terminated cases. The active lawsuits, including those against Sercomm Corporation and Toshiba Corporation, suggest that Encryptawave is enforcing this patent against companies involved in wireless communication and networking devices. The core issue likely revolves around whether these companies’ products implement similar dynamic encryption and authentication mechanisms, potentially infringing on the patented technology.
Potential Related Patent References for US7233664B2
#1. KR20000017575A
This patent, filed on August 27, 1999, describes a method for secure authentication between wireless communication network nodes by establishing a session key through mutual authentication. The system involves the exchange of authentication keys and node identifiers between a mobile station and a network, ensuring synchronized key regeneration. It introduces the use of an A-key and SSD (Shared Secret Data) to authenticate nodes and manage encryption keys dynamically.
Key Features of this Related Patent:
- Secure authentication between wireless communication nodes – The reference describes a method for secure authentication, ensuring mutual verification between a mobile station and a network, aligning with the authentication mechanism in US7233664B2.
- Node identifier comprises an address and an initial authentication key – It introduces an A-key and SSD as identifiers for authentication, which partially aligns with the node identifier structure in US7233664B2.
- Authentication key is synchronously regenerated – The reference explains that the session key is regenerated at both the mobile station and the network node using shared data and random numbers, similar to the dynamic authentication key regeneration in US7233664B2.
Which features of US7233664B2 are disclosed by KR20000017575A?
| Key feature of claim 1 | Disclosure status |
| A method provides secure authentication between wireless communication network nodes | Fully Disclosed |
| A node identifier comprises an address and an initial authentication key | Partially Disclosed |
| The node identifier is installed at a first network node | Fully Disclosed |
| The node identifier is stored at a second network node | Fully Disclosed |
| Node identifier information is sent from first network node to second network node | Fully Disclosed |
| An authentication key is synchronously regenerated at two network nodes based on node identifier information | Fully Disclosed |
Key excerpt from KR20000017575A:
“The root key, known as the A-key, is stored in the mobile station and transmitted securely to the VLR, where it is used for authentication and key generation. The session key is then synchronously regenerated at both network nodes using shared secret data (SSD) and random numbers.”
#2. US5706347A
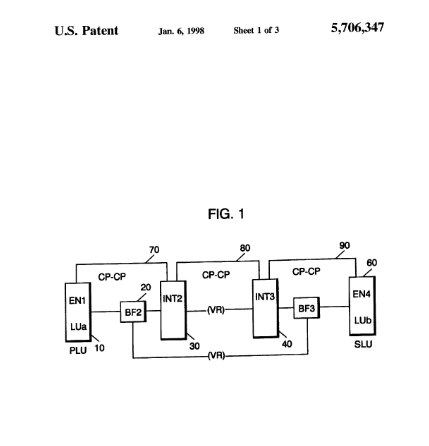
This patent, filed on November 3, 1995, describes a process for authenticating computer network nodes using cryptographic techniques to ensure secure communication. The invention focuses on verifying the identity of a receiving node before transmitting sensitive data. It introduces the use of session keys and master keys for encryption but does not explicitly define a node identifier as an address and an initial authentication key.
Source: GPS
Key Features of this Related Patent:
- Secure authentication between wireless communication nodes – The reference describes an authentication process for computer network nodes, ensuring secure communication, which aligns with the authentication system in US7233664B2.
- Node identifier installation and storage – It discusses generating and storing session keys at originating and destination nodes, which partially aligns with the concept of installing and storing node identifiers in US7233664B2.
- Transmission of node identifier information – The reference describes the transmission of session keys between network nodes, corresponding to the feature of sending node identifier information.
Which features of US7233664B2 are disclosed by US5706347A?
| Key feature of claim 1 | Disclosure status |
| A method provides secure authentication between wireless communication network nodes | Fully Disclosed |
| The node identifier is installed at a first network node | Partially Disclosed |
| The node identifier is stored at a second network node | Partially Disclosed |
| Node identifier information is sent from first network node to second network node | Fully Disclosed |
Key excerpt from US5706347A:
“In the next step in the session establishment process, the SLU decrypts the session cryptography key (KS) and generates an 8-byte initial chaining value (ICV) which is a random number ‘seed’ value that is put in the BIND response message to establish cryptographic communication.”
#3. US6292896B1
This patent, filed on January 22, 1997, describes a method for authenticating entities within a network and generating session keys for secure communication. The system involves a requesting node and an authenticating node, where authentication is performed using one-time passwords and session keys. It ensures that both entities derive a shared session key without transmitting it over the network, reducing security risks.
Key Features of this Related Patent:
- Secure authentication between wireless communication nodes – The reference outlines an authentication mechanism between network nodes using cryptographic verification, aligning with US7233664B2’s secure authentication process.
- Storage and transmission of node identifiers – It describes the use of user ID (UID), application ID (AID), and a signon key (K) for authentication, which is stored at both the requesting and authenticating nodes, partially aligning with US7233664B2.
- Synchronous key regeneration – The session key is regenerated at both the requesting node and the authenticating node without transmitting it, similar to the dynamic key regeneration in US7233664B2.
Which features of US7233664B2 are disclosed by US6292896B1?
| Key feature of claim 1 | Disclosure status |
| A method provides secure authentication between wireless communication network nodes | Fully Disclosed |
| A node identifier comprises an address and an initial authentication key | Partially Disclosed |
| The node identifier is installed at a first network node | Fully Disclosed |
| The node identifier is stored at a second network node | Fully Disclosed |
| Node identifier information is sent from first network node to second network node | Partially Disclosed |
| An authentication key is synchronously regenerated at two network nodes based on node identifier information | Fully Disclosed |
Key excerpt from US6292896B1:
“Both parties now have knowledge of the session key without having to transmit it across a network or via some alternate channel. The session key can be used to encrypt messages between the client (the function that initially signs on) and the target application, ensuring secure communication.”
#4. US6064741A
This patent, filed on October 10, 1997, describes a method for the mutual authentication of a user computer and a network computer, ensuring secure key exchange. The invention involves explicit identity verification, key agreement, and synchronous regeneration of session keys using cryptographic techniques. The process ensures that both parties establish a shared key without exposing it to interception.
Key Features of this Related Patent:
- Secure authentication between wireless communication nodes – The reference describes a mutual authentication process, ensuring both the user computer and the network computer verify each other’s identity, which aligns with US7233664B2.
- Transmission of node identifier information – The method includes exchanging messages that contain key-derived values between the user and network computer units, corresponding to the feature of sending node identifier information.
- Synchronous authentication key regeneration – The system ensures that session keys are regenerated at both network nodes using exchanged values, aligning with the dynamic key synchronization approach in US7233664B2.
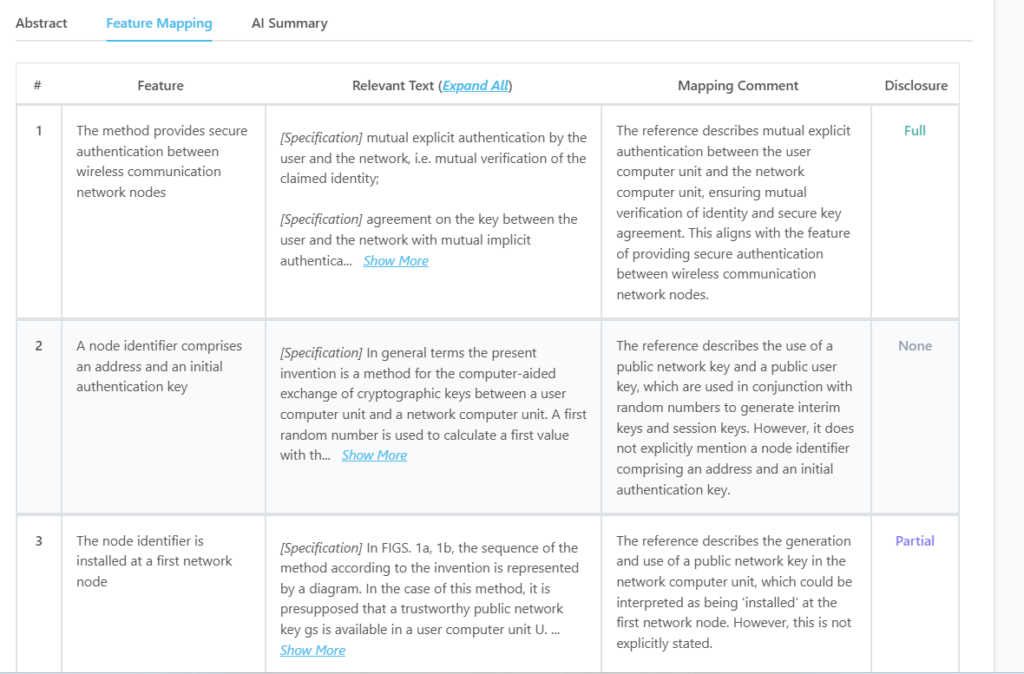
Here’s what the mapping from the tool for this particular patent looks like:
Source: GPS
Which features of US7233664B2 are disclosed by US6064741A?
| Key feature of claim 1 | Disclosure status |
| A method provides secure authentication between wireless communication network nodes | Fully Disclosed |
| The node identifier is installed at a first network node | Partially Disclosed |
| The node identifier is stored at a second network node | Partially Disclosed |
| Node identifier information is sent from first network node to second network node | Fully Disclosed |
| An authentication key is synchronously regenerated at two network nodes based on node identifier information | Fully Disclosed |
Key excerpt from US6064741A:
“A first random number is used to calculate a first value with the aid of a first key. The first value is transmitted to the network computer unit, where it is used in combination with a second key to generate a session key. The session key is thus synchronously regenerated at both units without direct transmission.”
#5. EP0393806A2
This patent, filed on January 5, 1990, describes a public key cryptographic system that enables secure authentication and key exchange without relying on a key distribution center. The invention ensures secrecy and identity authentication through the exchange of digitally signed composite quantities between communication nodes. It also establishes session keys synchronously at both nodes based on identifier information.
Key Features of this Related Patent:
- Secure authentication between wireless communication nodes – The reference describes a cryptographic system for mutual authentication and secure key exchange, aligning with US7233664B2’s approach to secure authentication.
- Node identifier structure and transmission – It introduces a unique device identifier (IDa, IDb) and a digitally signed composite quantity, fulfilling the requirement of an address and an initial authentication key for authentication. These identifiers are exchanged and stored at the second network node.
- Synchronous key regeneration – The authentication key (session key) is regenerated at both network nodes using exchanged node identifier information, similar to the dynamic key synchronization in US7233664B2.
Which features of US7233664B2 are disclosed by EP0393806A2?
| Key feature of claim 1 | Disclosure status |
| A method provides secure authentication between wireless communication network nodes | Fully Disclosed |
| A node identifier comprises an address and an initial authentication key | Fully Disclosed |
| The node identifier is installed at a first network node | Fully Disclosed |
| The node identifier is stored at a second network node | Fully Disclosed |
| Node identifier information is sent from first network node to second network node | Fully Disclosed |
| An authentication key is synchronously regenerated at two network nodes based on node identifier information | Fully Disclosed |
Key excerpt from EP0393806A2:
“Before secure communications are established, two devices exchange these digitally signed quantities, which may then be easily transformed into unsigned form. The resulting identifier information is used to authenticate the other device and to generate a session key synchronously at both nodes.”
Feature Comparison Table
| Key feature of Claim 1 | KR20000017575A | US5706347A | US6292896B1 | US6064741A | EP0393806A2 |
| A method provides secure authentication between wireless communication network nodes | Fully Disclosed | Fully Disclosed | Fully Disclosed | Fully Disclosed | Fully Disclosed |
| A node identifier comprises an address and an initial authentication key | Partially Disclosed | Not Disclosed | Partially Disclosed | Not Disclosed | Fully Disclosed |
| The node identifier is installed at a first network node | Fully Disclosed | Partially Disclosed | Fully Disclosed | Partially Disclosed | Fully Disclosed |
| The node identifier is stored at a second network node | Fully Disclosed | Partially Disclosed | Fully Disclosed | Partially Disclosed | Fully Disclosed |
| Node identifier information is sent from first network node to second network node | Fully Disclosed | Fully Disclosed | Partially Disclosed | Fully Disclosed | Fully Disclosed |
| An authentication key is synchronously regenerated at two network nodes based on node identifier information | Fully Disclosed | Not Disclosed | Fully Disclosed | Fully Disclosed | Fully Disclosed |
How to find Related Patents using Global Patent Search?
Finding related patents is essential in assessing a patent’s validity. The Global Patent Search (GPS) tool simplifies this process by providing a structured approach to identifying relevant related patent references. Here’s how GPS can help:
- Search by patent number or description – Instantly retrieve related patents by entering a specific patent number or using relevant technical keywords.
- Leverage feature mapping – Compare the core features of a subject patent against existing patents to identify potential overlaps.
- Review matching results – Analyze a curated list of related patent references that align with the features of the subject patent.
- Analyze detailed reports – View comprehensive feature-matching reports that highlight similarities and differences between patents.
- Make confident decisions – Use data-driven insights to assess the strength of a patent’s claims in litigation or invalidation proceedings.
By using GPS, patent professionals can efficiently uncover potential related patents, ensuring a thorough and precise evaluation of a patent’s validity.
Take the Guesswork out of Related Patent Research
Patent disputes are complex, but finding related patent doesn’t have to be. The Global Patent Search (GPS) tool provides:
- Instant results – Eliminate the need for time-consuming manual searches.
- Accurate feature mapping – Identify key overlaps with precision.
- Data-driven insights – Strengthen your case with related patent overlap.
Ensure you have the strongest related patent references to support your case. Unlock the power of Global Patent Search and stay ahead in patent litigation!
Disclaimer: The information provided in this article is for informational purposes only and should not be considered legal advice. The related patent references mentioned are preliminary results from the Global Patent Search (GPS) tool and do not guarantee legal significance. For a comprehensive related patent analysis, we recommend conducting a detailed search using GPS or consulting a patent attorney.