Could this patent be the key to winning a high-stakes legal battle? VPN Technology Holdings, LLC is currently locked in an active lawsuit with Red Hat, Inc., involving US7844718B2. This patent plays a crucial role in the way modern virtual private networks (VPNs) manage secure communication.
This patent addresses a unique method for establishing a secure communication session over a network, essential for protecting data and ensuring private internet traffic between users and servers. With VPN technology at the heart of the digital world’s security infrastructure, US7844718B2 is a potential turning point in this litigation, given its broad claims that it could impact various network systems.
In this article, we will explore the details of this patent, why it’s being targeted in the ongoing dispute, and how it might shape the legal landscape for VPN technology. Furthermore, we will highlight how Global Patent Search can help you identify related patents, giving you the tools to navigate patent litigation with confidence.
Understanding Patent US7844718B2
Patent US7844718B2 discloses a system and method for automatically configuring a remote computer to establish a VPN connection with a network. The invention focuses on simplifying the process of setting up VPN access for remote users by generating an executable file that, when run on the remote computer, automatically configures the system to establish the connection. This method eliminates the need for manual configuration, reducing errors and delays in setting up remote connections.
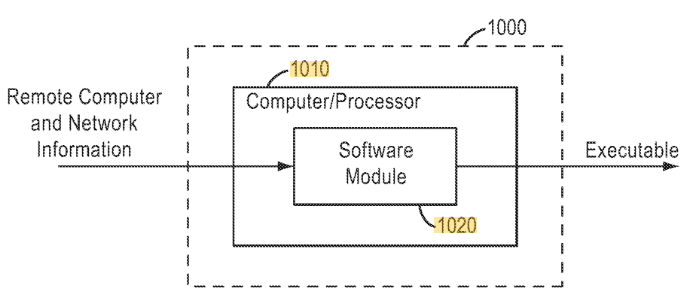
Source: US7844718B2
Its four key features are:
#1. Automatic configuration of remote computer: The system automatically configures the remote computer by generating an executable file that adjusts the computer’s settings to establish a VPN connection.
#2. Executable file for configuration: A configuration generator creates an executable file that updates the necessary settings on the remote computer, including network parameters such as IP addresses, DNS, WINS, and gateway addresses.
#3. Simplified deployment: The executable file can be deployed to the remote computer via email or downloaded from a website, making it easy for remote users to initiate the configuration process.
#4. Self-deleting executable: After the executable file is configured on the remote computer, it self-deletes, ensuring no residual files remain and further enhancing security.
The US7844718B2 patent is a key piece of VPN technology that plays a critical role in the ongoing litigation between VPN Technology Holdings, LLC and Red Hat, Inc. The patent provides a streamlined approach to configuring remote computers for VPN access, an essential feature for secure enterprise communications. Given its potential application across various industries, the patent could have significant implications for the defendants in the case. Configuring remote access securely and automatically through this system is central to the dispute.
Related Patent Reference for US7844718B2
#1. US5784555A
This patent, filed on April 18, 1996, by Microsoft Corporation, describes a system for automating the configuration and checking of system settings for Internet connections. It focuses on using an installer program to manage and configure network settings, which involves accessing a network database and configuring network protocols to facilitate a seamless connection.
Key Features of this Related Patent:
- Automated network configuration – US5784555A automates the network configuration process, much like US7844718B2, but does not explicitly handle creating an executable file to configure VPN connections.
- Installer program for network setup – Similar to the installer process in US7844718B2, it discusses a system where a program is executed to automate network configuration tasks. However, it lacks the specific creation of executable files for remote VPN configuration.
- Internet set-up wizard – The patent refers to an Internet setup wizard that automates the installation of Internet connections. While it includes automation steps, it does not fully align with the unique automated VPN setup described in US7844718B2.
Which features of US7844718B2 are disclosed by US5784555A?
| Key Feature of Claim 1 | Disclosure Status |
| Initiating an installer program with an empty binary file at a network administrator computer | Partially Disclosed |
Key Excerpt from US5784555A:
“The invention described herein automates the configuration and installation of Internet devices. This process involves using a software wizard that simplifies the setup of network connections, ensuring that the correct configuration is applied to devices in the network. It enables the automatic configuration of network protocols required for proper communication between devices.”
#2. JPH06332826A
This patent, filed on May 21, 1993, by NEC Corporation, describes a method for network management that involves encryption and access control to manage user permissions for accessing network services. It discusses the automation of access rights and the management of users’ credentials to ensure secure communication across networked devices.
Key Features of this Related Patent:
- Access control for networked devices – This reference deals with user access rights management, similar to the security concerns addressed in US7844718B2, but it does not specifically involve the configuration of remote computers for VPN connections.
- User credential encryption – The patent encrypts user credentials for access control, which aligns with the credential encoding feature in US7844718B2, though it does not focus on VPN-specific configurations.
- Automated network configuration for user access – The reference automates the setup of network access but does not address the specific steps involved in configuring remote systems for VPN communication, as described in US7844718B2.
Which features of US7844718B2 are disclosed by JPH06332826A?
| Key Feature of Claim 1 | Disclosure Status |
| Accessing a network database to extract configuration data representing binary settings of network topology and remote computer | Partially Disclosed |
| Coding and automatically transmitting WAN login credentials to VPN server | Partially Disclosed |
| Coding and automatically transmitting LAN login credentials to domain controller | Partially Disclosed |
| Encoding credentials to be hidden from user | Fully Disclosed |
Key Excerpt from JPH06332826A:
“In the access right file, the user ID, password, role net use right, and in-net use right of the user who is permitted to use the computer are encrypted and registered, ensuring secure access management and encryption of the necessary credentials.”
#3. US6330562B1
This patent, filed on January 29, 1999, by IBM (International Business Machines Corporation), describes a system and method for managing security objects, particularly within a Virtual Private Network (VPN) environment. It focuses on the dynamic negotiation and maintenance of secure VPN connections using a data model abstracting VPN security policies.
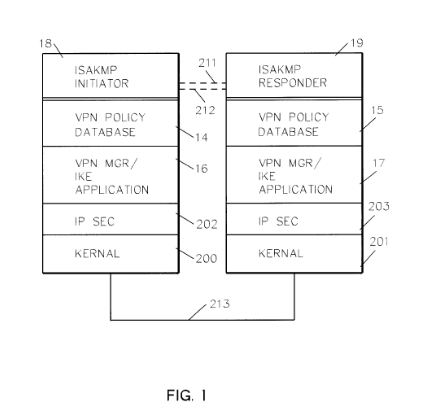
Source: US6330562B1
Key Features of this Related Patent:
- Dynamic VPN security management – US6330562B1 addresses VPN security management, which involves dynamic negotiation of secure connections, similar to the VPN configuration concerns in US7844718B2. However, it lacks the creation of executable files for configuring remote computers.
- Policy-based configuration – This reference focuses on policy-driven VPN management, whereas US7844718B2 emphasizes the automation of configuration for remote computers, including RAS settings and VPN connection establishment.
- Security object abstraction for VPN nodes – The abstraction of security policies for VPN nodes in US6330562B1 aligns with some aspects of network security in US7844718B2, but it does not address the specific step of automating the configuration of remote computers to establish VPN connections.
Which features of US7844718B2 are disclosed by US6330562B1?
| Key Feature of Claim 1 | Disclosure Status |
| Accessing a network database to extract configuration data representing binary settings of network topology and remote computer | Partially Disclosed |
| Creating connection profile with network addressing information | Partially Disclosed |
Key Excerpt from US6330562B1:
“In accordance with the invention, a data model is provided for abstracting customer-defined VPN security policy information. By employing this model, a VPN node can dynamically negotiate, create, and maintain secure connections, while managing the policies required for secure communication across the network.”
#4. TW498278B
This patent, filed on February 7, 1998, by Google LLC and IBM, describes a system for general user authentication in networked computers. It focuses on secure authentication processes, including transmitting user credentials between a client computer and a server.
Key Features of this Related Patent:
- Secure credential transmission – The patent discusses coding and transmitting user credentials for authentication, which partially aligns with the feature in US7844718B2 related to WAN and LAN login credentials.
- User credential encryption – The reference describes encoding credentials to be hidden from the user, ensuring security in authentication processes.
- Focus on authentication rather than configuration – While TW498278B handles secure credential exchange, it does not discuss deploying an executable file or configuring remote computers for VPN access.
This is how feature mapping from the tool looks like:
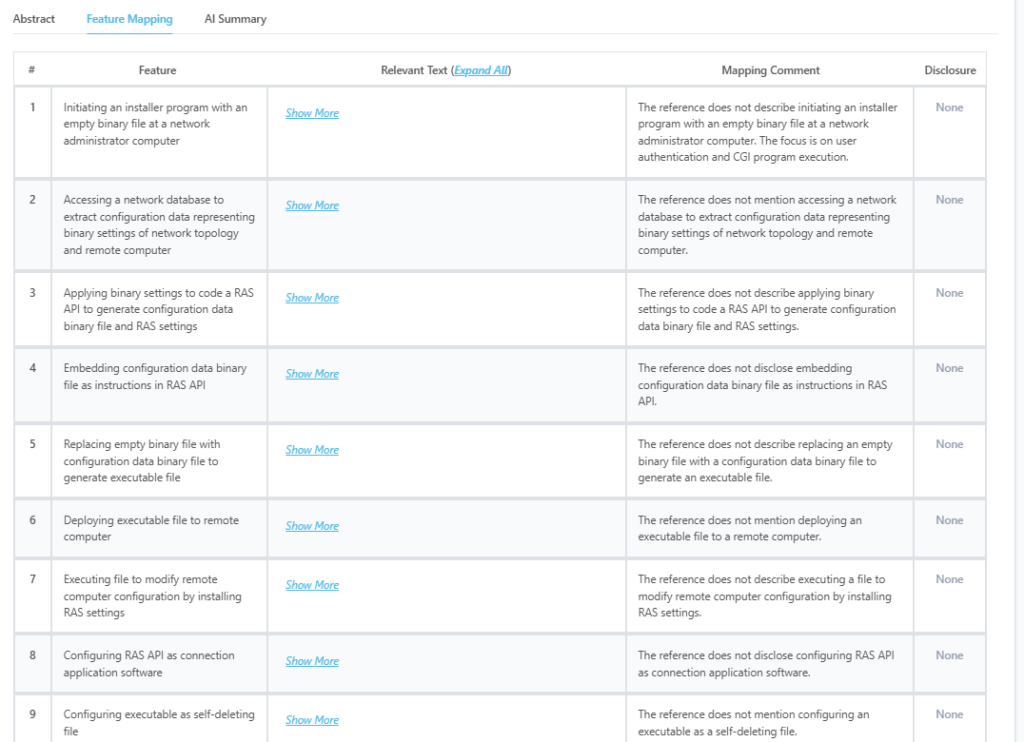
Source: GPS
Which features of US7844718B2 are disclosed by TW498278B?
| Key Feature of Claim 1 | Disclosure Status |
| Coding and automatically transmitting WAN login credentials to VPN server | Partially Disclosed |
| Coding and automatically transmitting LAN login credentials to domain controller | Partially Disclosed |
| Encoding credentials to be hidden from user | Fully Disclosed |
Key Excerpt from TW498278B:
“As mentioned above, during each CGI execution request, the user information is uploaded to the server, and the user information together with the result of each CGI program is sent back to the client computer. Therefore, credentials are managed securely and hidden from the user.”
#5. US6490687B1
This patent, filed on March 12, 1999, by NEC Corporation, describes a system for login permission with improved security. It focuses on encrypted authentication processes, particularly through the use of a PC-card pager for user authentication.
Key Features of this Related Patent:
- Secure login authentication – The reference describes a system where encrypted authentication information is transmitted between devices, similar to the secure credential transmission in US7844718B2.
- Use of external authentication devices – This patent leverages external authentication methods (PC-card pagers), which is different from the automated software-based configuration process in US7844718B2.
- Encryption-based authentication – The reference discusses encrypting authentication data but does not focus on configuring remote computers for VPN access.
Which features of US7844718B2 are disclosed by US6490687B1?
| Key Feature of Claim 1 | Disclosure Status |
| Encoding credentials to be hidden from user | Partially Disclosed |
Key Excerpt from US6490687B1:
“The encrypted authentication information is sent back to the mobile terminal and is then transmitted to the stationary switched network and further to the host computer. This process ensures that user credentials remain secure during transmission.”
Feature Comparison Table
| Key Feature of Claim 1 | US5784555A | JPH06332826A | US6330562B1 | TW498278B | US6490687B1 |
| Initiating an installer program with an empty binary file at a network administrator computer | Partially Disclosed | Not Disclosed | Not Disclosed | Not Disclosed | Not Disclosed |
| Accessing a network database to extract configuration data representing binary settings of network topology and remote computer | Not Disclosed | Partially Disclosed | Partially Disclosed | Not Disclosed | Not Disclosed |
| Applying binary settings to code a RAS API to generate configuration data binary file and RAS settings | Not Disclosed | Not Disclosed | Not Disclosed | Not Disclosed | Not Disclosed |
| Embedding configuration data binary file as instructions in RAS API | Not Disclosed | Not Disclosed | Not Disclosed | Not Disclosed | Not Disclosed |
| Replacing empty binary file with configuration data binary file to generate executable file | Not Disclosed | Not Disclosed | Not Disclosed | Not Disclosed | Not Disclosed |
| Deploying executable file to remote computer | Not Disclosed | Not Disclosed | Not Disclosed | Not Disclosed | Not Disclosed |
| Executing file to modify remote computer configuration by installing RAS settings | Not Disclosed | Not Disclosed | Not Disclosed | Not Disclosed | Not Disclosed |
| Configuring RAS API as connection application software | Not Disclosed | Not Disclosed | Not Disclosed | Not Disclosed | Not Disclosed |
| Configuring executable as self-deleting file | Not Disclosed | Not Disclosed | Not Disclosed | Not Disclosed | Not Disclosed |
| Executing file so RAS API establishes VPN connection | Not Disclosed | Not Disclosed | Not Disclosed | Not Disclosed | Not Disclosed |
| Creating connection profile with network addressing information | Not Disclosed | Not Disclosed | Partially Disclosed | Not Disclosed | Not Disclosed |
| Coding and automatically transmitting WAN login credentials to VPN server | Not Disclosed | Not Disclosed | Not Disclosed | Partially Disclosed | Not Disclosed |
| Coding and automatically transmitting LAN login credentials to domain controller | Not Disclosed | Partially Disclosed | Not Disclosed | Partially Disclosed | Not Disclosed |
| Encoding credentials to be hidden from user | Not Disclosed | Fully Disclosed | Not Disclosed | Fully Disclosed | Partially Disclosed |
| Automatically deleting executable file after VPN connection termination | Not Disclosed | Not Disclosed | Not Disclosed | Not Disclosed | Not Disclosed |
How to Find Related Patents Using Global Patent Search
Finding related patents is crucial in evaluating a patent’s validity, especially in litigation cases. The Global Patent Search (GPS) tool streamlines this process with its advanced search and comparison features, making it an indispensable asset for legal teams and patent analysts. This is how GPS helps in identifying related patents:
Search by patent number or description – Instantly retrieve relevant patents related to a specific technology or invention.

Source: GPS
Leverage feature mapping – Compare key features of the subject patent against existing patents for a detailed analysis.
Review matching results – Browse a curated list of related patents that may impact the patent’s validity under litigation.
Analyze detailed reports – Gain insights into how each reference patent aligns with or diverges from the claims of the subject patent.
Make confident decisions – Use data-driven insights to refine legal strategies and strengthen a case.
With GPS, patent research becomes efficient and precise, allowing legal teams to focus on the most relevant references when assessing the strength of a patent.
Take the Guesswork Out of Related Patent Research
Patent disputes are complex, but finding related patents doesn’t have to be. The Global Patent Search (GPS) tool provides a fast, accurate, and data-driven approach to identifying relevant patents that could impact the validity of US7844718B2.
Here are the reasons for using GPS for patent analysis:
- Instant results – No more time-consuming manual searches. Retrieve related patents within seconds.
- Accurate feature mapping – Identify key overlaps between patents with precision.
- Data-driven insights – Strengthen your case with comprehensive and reliable patent comparisons.
Ensure you have the most strategic and impactful related patent references at your disposal. Gain a competitive edge. Start your search with Global Patent Search today!
Disclaimer: The information provided in this article is for informational purposes only and should not be considered legal advice. The related patent references mentioned are preliminary results from the Global Patent Search (GPS) tool and do not guarantee legal significance. For a comprehensive related patent analysis, we recommend conducting a detailed search using GPS or consulting a patent attorney.